What Is A Domain Controller: Safeguarding Sensitive Information in Corporations
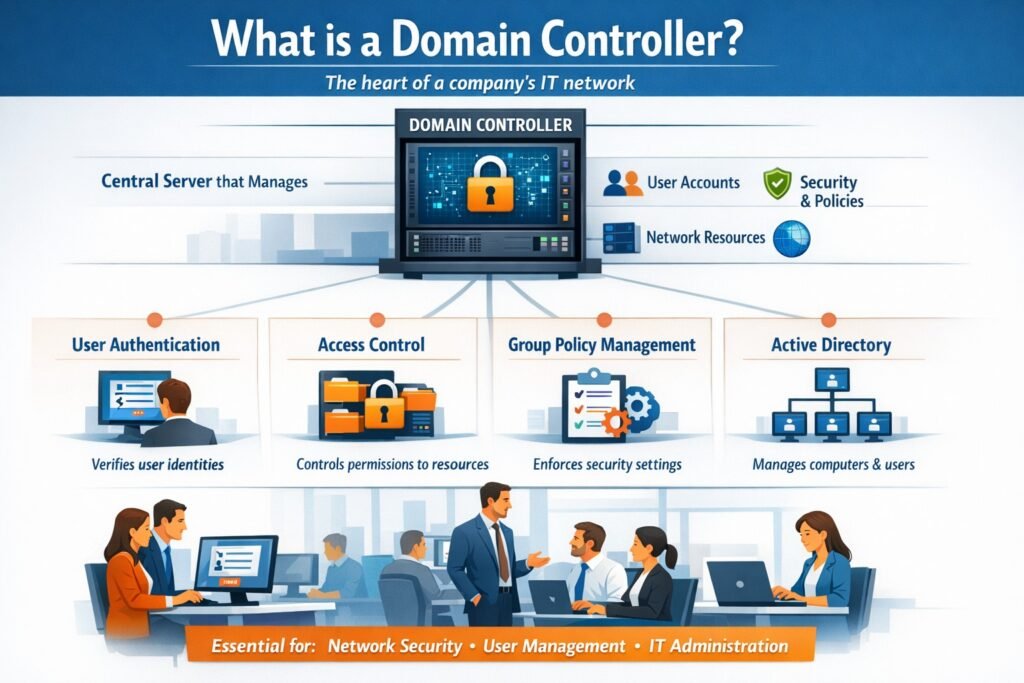
Domain controllers are crucial components in managing IT infrastructure within large organizations. They are responsible for authenticating users and managing access to network resources, ensuring that security protocols are upheld while facilitating smooth operations. Understanding the role of domain controllers is essential for organizations looking to enhance their network security and efficiency. In this article, we will delve into the intricacies of domain controllers, their functions, and how they contribute to the overall security and management of enterprise networks.
Understanding the Role of a Domain Controller in IT Systems
A domain controller (DC) is a server in a network that responds to security authentication requests within a Windows domain. This role is pivotal for managing user accounts and enforcing security policies. By acting as a central point for user access, domain controllers help maintain an organized structure for user data, permissions, and resources. This organization streamlines operations, especially in large enterprises where numerous users and devices are interconnected.
The domain controller also plays a critical role in network management. It is responsible for maintaining a directory service, which includes information about network resources such as printers, computers, and shared files. By centralizing this information, domain controllers make it easier for IT administrators to manage resources efficiently, reducing the risk of mismanagement or security breaches.
In the context of scalability, domain controllers can also support multiple domains, allowing organizations to segregate and manage different departments or subsidiaries more effectively. This flexibility enables enterprises to cater to diverse needs within their IT infrastructure, ensuring that each domain can operate independently while still being part of the larger organizational network.
Key Functions and Responsibilities of a Domain Controller
The primary function of a domain controller is user authentication, which verifies the identity of users when they attempt to access network resources. This process is typically carried out using protocols such as Kerberos or NTLM, which provide secure methods for validating user credentials. By ensuring that only authorized individuals gain access, domain controllers play a significant role in safeguarding sensitive information.
Another crucial responsibility is the management of Group Policy Objects (GPOs). These are essential for configuring settings across a network, from password policies to software installation requirements. By centralizing the management of these settings, domain controllers help enforce uniform security policies, reducing the likelihood of vulnerabilities due to inconsistent configurations across devices.
Additionally, domain controllers facilitate the creation and management of user accounts. IT administrators can easily add, modify, or delete user accounts through the domain controller, streamlining the onboarding and offboarding process. This capability is vital for maintaining security and ensuring that access permissions are kept up-to-date, particularly in large organizations where employee turnover may be high.
How Domain Controllers Manage User Authentication
User authentication is a multi-layered process that begins when a user attempts to log in to a network resource. The domain controller verifies the user’s credentials against its database, ensuring that the individual is who they claim to be. This process is not just about validating usernames and passwords; it often includes additional security measures such as two-factor authentication.
Once authentication is successful, the domain controller issues a security token to the user. This token contains information about the user’s permissions and access rights within the network. It allows users to access various resources without needing to re-enter credentials each time, improving user experience while maintaining security.
Domain controllers also play a key role in implementing security policies related to user authentication. For instance, they can enforce password complexity requirements, account lockout policies, and session timeouts. By managing these policies centrally, domain controllers ensure that all users adhere to the organization’s security standards, reducing the risks of unauthorized access.
The Relationship Between Domain Controllers and Active Directory
Active Directory (AD) is a directory service developed by Microsoft for Windows domain networks, and domain controllers are its backbone. Every domain controller holds a copy of the Active Directory database, which contains all user and computer accounts as well as their associated permissions. This synchronized structure allows for quick access and management of resources across the network.
The integration of domain controllers and Active Directory simplifies resource management. For example, when a new user is added to the system, the domain controller updates the Active Directory, ensuring that the user’s access rights are reflected immediately across all relevant systems. This real-time updating capability is essential for maintaining security and operational efficiency in organizations.
Additionally, Active Directory’s replication feature ensures that changes made on one domain controller are propagated to others. This redundancy not only enhances availability but also ensures that all domain controllers have the most up-to-date information, which is critical for consistent user authentication and resource management.
Domain Controllers: Enhancing Network Security and Access
One of the most significant advantages of using domain controllers is their impact on network security. By centralizing authentication and authorization processes, organizations can implement stricter security measures more effectively. Domain controllers can monitor login attempts, flagging suspicious activities and automatically locking accounts after multiple failed attempts, thereby mitigating the risk of breaches.
Moreover, domain controllers enable the implementation of security policies that can be tailored to different user groups within an organization. For example, high-level executives may have access to more sensitive data compared to entry-level employees. By using Group Policy settings, IT administrators can configure permissions based on these roles, enhancing security without compromising accessibility.
Another aspect of security comes from the ability to audit and monitor user activity. Domain controllers can log authentication events, providing a clear record of who accessed what and when. This logging capability is crucial for compliance with regulations and internal audits, as organizations can demonstrate accountability and track potential security incidents effectively.
Real-World Use Cases of Domain Controllers in Enterprises
In large enterprises, domain controllers are utilized to manage diverse and extensive networks. For instance, a multinational corporation may have multiple branches across different countries, each requiring tailored access to company resources. Domain controllers facilitate this by allowing each branch to have its own domain while still being part of the corporate network.
Consider a healthcare organization that needs to protect sensitive patient information. Domain controllers can enforce strict access controls, ensuring only authorized medical staff can access patient records. This capability not only adheres to regulatory requirements but also builds trust with patients regarding the confidentiality of their data.
Moreover, retail companies can benefit from domain controllers by managing multiple stores under a unified system. With a central domain controller, the corporate headquarters can easily deploy software updates, enforce security settings, and manage user accounts across all locations, streamlining operations and enhancing security.
Common Challenges and Solutions for Domain Controllers
Despite their advantages, domain controllers come with their own set of challenges. One of the most prevalent issues is the risk of a single point of failure. If a domain controller goes down, it can disrupt access to network resources for all users. To mitigate this, organizations should implement multiple domain controllers within their infrastructure to provide redundancy and ensure high availability.
Another challenge lies in managing domain controller performance. As organizations grow, the load on domain controllers increases, potentially leading to slower authentication times. Regularly monitoring performance metrics and scaling infrastructure accordingly can help address this issue. Additionally, implementing load balancing techniques can distribute the authentication requests evenly across multiple domain controllers, enhancing overall performance.
Security vulnerabilities are also a concern for domain controllers, as they are prime targets for cyberattacks. Organizations should employ multifactor authentication, regular software updates, and security patches to protect these critical components. Furthermore, conducting regular security audits and penetration testing can help identify and remediate vulnerabilities before they can be exploited.
Future Trends in Domain Controller Technology and Management
As technology evolves, so do the capabilities and functions of domain controllers. One notable trend is the integration of cloud services with traditional on-premises infrastructure. Organizations are increasingly adopting hybrid models that combine local domain controllers with cloud-based solutions, allowing for greater flexibility and scalability.
Another emerging trend is the shift toward automation in managing domain controllers. With advancements in artificial intelligence and machine learning, organizations can automate routine tasks such as user provisioning, password resets, and security updates. This automation not only increases efficiency but also reduces the potential for human error.
Finally, the rising emphasis on zero-trust security models is changing how domain controllers operate. Organizations are moving away from perimeter-based security to focus on verifying every user and device attempting to access resources. Domain controllers will play a crucial role in this model, ensuring that access is granted based on rigorous authentication processes regardless of the user’s location.
Domain controllers are indispensable in modern IT infrastructures, particularly within large enterprises. They provide the necessary framework for managing user authentication, access control, and security policies. Understanding their functions and capabilities can empower organizations to optimize their network security and streamline operations effectively. As technology continues to evolve, staying informed about trends and best practices will be essential for leveraging the full potential of domain controllers.
Below is an enterprise-focused case study suitable for inclusion within the blog. It is written to reinforce the strategic value of domain controllers rather than provide a purely technical walkthrough.
Case Study: Strengthening Identity Control and Security in a Global Enterprise
Background
A multinational professional services organization with over 18,000 employees across North America, Europe, and Asia-Pacific was experiencing growing challenges with identity management and network security. Rapid expansion through acquisitions had resulted in fragmented IT environments, inconsistent access controls, and multiple unmanaged authentication systems. These gaps increased operational risk, complicated audits, and slowed onboarding for new employees.
Senior leadership tasked the IT and security teams with consolidating identity management while improving security resilience and operational efficiency.
The Challenge
The organization faced several critical issues:
-
Inconsistent user authentication across regions and subsidiaries
-
Limited visibility into user permissions and access rights
-
Increased risk of credential misuse and unauthorized access
-
Manual, error-prone user provisioning and deprovisioning processes
-
Audit findings related to weak access governance and policy enforcement
Without a centralized authority for identity and access management, enforcing enterprise-wide security policies was becoming unsustainable.
The Solution
The organization redesigned its identity architecture around a standardized Active Directory environment supported by strategically deployed domain controllers. Key initiatives included:
-
Consolidating disparate identity systems into a unified domain structure
-
Deploying redundant domain controllers across regions to ensure high availability
-
Implementing role-based access controls aligned with job functions
-
Centralizing Group Policy enforcement for security baselines and compliance
-
Integrating on-premises domain controllers with cloud identity services to support hybrid workloads
This approach established domain controllers as the authoritative source for authentication, authorization, and policy enforcement across the enterprise.
The Results
Within twelve months, the organization achieved measurable improvements:
-
Reduced onboarding time for new employees by over 40 percent
-
Improved audit outcomes with clear evidence of access control enforcement
-
Lowered security incident rates related to credential misuse
-
Increased operational resilience through redundancy and failover
-
Enhanced visibility for IT leadership into user access, permissions, and policy compliance
Most importantly, the organization regained confidence in its ability to manage identity and access at scale without introducing unnecessary friction for business users.
Business Impact
By investing in a robust domain controller architecture, the enterprise transformed identity management from an operational liability into a strategic capability. Centralized authentication enabled stronger security, faster growth, and improved regulatory alignment. Domain controllers became a foundational control point supporting both legacy systems and modern cloud-based services.
Key Takeaway
For large organizations, domain controllers are not simply infrastructure components—they are critical governance mechanisms. When properly designed and integrated, they provide the control, visibility, and scalability required to secure enterprise networks while supporting ongoing business transformation.
Frequently Asked Questions (FAQ)
What is a domain controller?
A domain controller (DC) is a server that manages authentication, authorization, and security policy enforcement within a Windows domain. It validates user credentials, controls access to network resources, and serves as the authoritative source for identity and access management across the enterprise network.
Why are domain controllers critical to enterprise IT environments?
Domain controllers provide centralized control over users, devices, and permissions, which is essential in large, distributed organizations. Without domain controllers, enterprises would struggle to enforce consistent security policies, manage identities at scale, or maintain reliable access controls across complex networks.
How does a domain controller improve network security?
Domain controllers enforce authentication protocols, password policies, account lockout rules, and group-based access controls. By centralizing these functions, they reduce the risk of unauthorized access, limit lateral movement within the network, and provide a structured framework for applying security controls consistently.
What role does Active Directory play in domain controllers?
Active Directory (AD) is the directory service that runs on domain controllers. It stores and organizes information about users, groups, computers, and network resources. Domain controllers use Active Directory to authenticate users and determine what resources they are permitted to access.
Can an organization have more than one domain controller?
Yes. Enterprises typically deploy multiple domain controllers to ensure redundancy, fault tolerance, and high availability. If one domain controller fails, others can continue authenticating users and enforcing policies, minimizing operational disruption.
How do domain controllers support scalability in large organizations?
Domain controllers enable scalability by supporting multiple domains, organizational units (OUs), and trust relationships. This structure allows enterprises to segment departments, regions, or subsidiaries while maintaining centralized governance and consistent security standards.
What happens if a domain controller goes offline?
If a single domain controller goes offline in an environment with redundancy, authentication requests are automatically handled by other available domain controllers. However, in environments with only one domain controller, outages can prevent users from logging in or accessing critical network resources.
How are domain controllers different from member servers?
A domain controller manages authentication and directory services, while a member server provides specific services such as file sharing, application hosting, or printing. Member servers rely on domain controllers to verify user identities and permissions before granting access.
Are domain controllers still relevant in cloud and hybrid environments?
Yes. In hybrid environments, domain controllers often integrate with cloud identity platforms such as Azure Active Directory to provide seamless identity management across on-premises and cloud resources. They remain a foundational component for enterprises transitioning to cloud-based architectures.
What best practices should enterprises follow when managing domain controllers?
Best practices include deploying multiple domain controllers, applying strict access controls, regularly patching and monitoring systems, securing administrative credentials, and placing domain controllers in protected network segments. These measures help ensure resilience, security, and long-term operational stability.
Conclusion
Domain controllers remain a foundational pillar of enterprise IT infrastructure, providing the centralized authentication, authorization, and policy enforcement that modern organizations depend on. By managing identities and access from a single, authoritative source, they enable consistent security controls, operational efficiency, and reliable user experiences across complex networks.
As enterprises scale, adopt hybrid architectures, and face increasingly sophisticated security threats, the role of the domain controller becomes even more strategic. Properly designed, secured, and maintained domain controller environments not only reduce risk and administrative overhead but also support long-term flexibility and growth. For organizations seeking to strengthen their network security posture and maintain control at scale, understanding and investing in robust domain controller architecture is not optional it is essential.
Hashtags: #DomainController #NetworkSecurity #ActiveDirectory #ITManagement #EnterpriseSolutions
External Source: Explore What Is a Domain Controller by SolarWinds? https://www.solarwinds.com/resources/it-glossary/domain-controller
Discover More great insights at www.pmresourcehub.com
Explore Free Project Management Templates https://pmresourcehub.com/library/
